Product Features
- Vulnerability Depth Mining
- Professional Assessment Report
- Vulnerability Repair and Verification
-
Under premise that normal operation of business system is not affected, attack path is formed by the security expert in series of security weaknesses, which can be used to achieve effect of simulated invasion and dig hidden security risks
-
In strict accordance with international security standards, comprehensive evaluation of application security situation, and provide vulnerability description, process details and repair solutions combined with application business scenarios
-
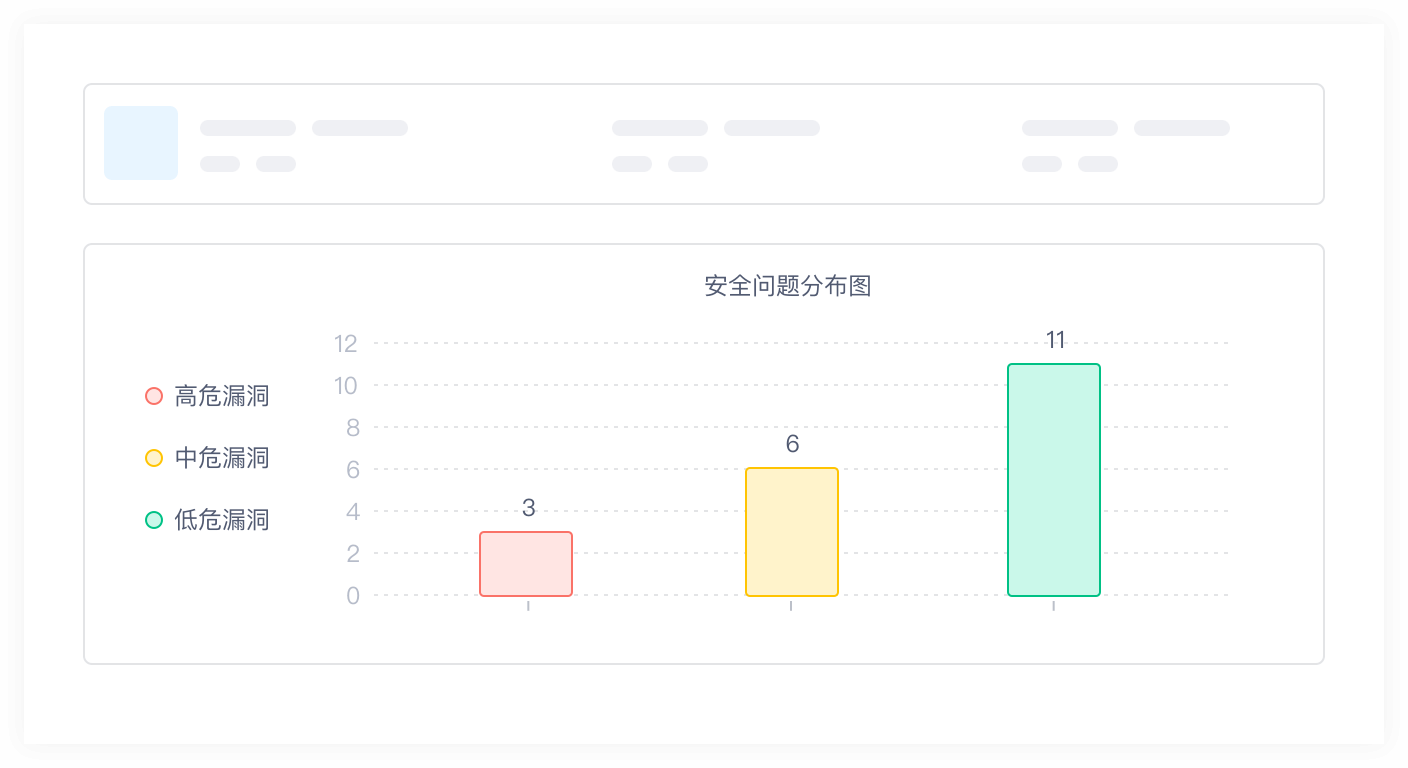
In view of security risks report, assist customer to repair, and retest repair results to fully verify effectiveness of vulnerability repair

Product Advantage
-

Quality Report Delivery
Before delivery of test report, project team has gone through triple review process of self-inspection, mutual inspection and quality auditor review, with strict quality control and high-quality report delivery
-

One-to-one Expert Service
Security experts one-to-one detailed report interpretation, it helps customers repair security vulnerabilities, solve security risks, at the same time, improve security awareness of customer technical personnel
-

Senior Security Team
Testin has worked as a cloud security testing expert in Microsoft and other enterprises, with cutting-edge security testing technology and independently developed security testing tools
Application Scenario
-

Business scenarios have high requirements for security, such as electronic transactions, online payments, etc. We hope to deeply detect security risks, solve problems from root and reduce security risks
-

Enterprises hope to deal with unsafe market situation, in order to protect business security and corporate image
-

Companies want to maximize security while controlling costs
